NSS Labs expose inadequate AV products.
SS Labs testing showed that 9 of 13 popular consumer anti-virus products tested failed to provide adequate protection against exploits targeting two recent critical Microsoft vulnerabilities.
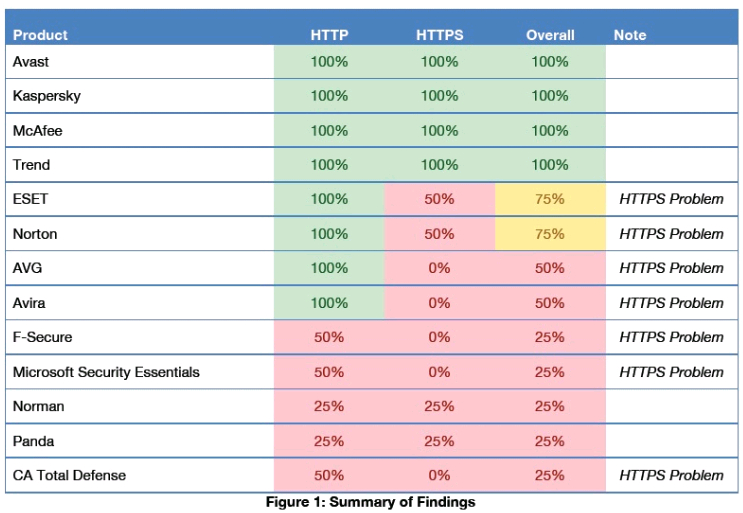
Only 4 vendors – Avast, Kaspersky, McAfee and Trend Micro – successfully blocked all attacks delivered over both HTTP and HTTPS.
"This particular exploit test was a small part of a much more comprehensive endpoint security test underway at NSS Labs that will be published next month," said Randy Abrams, Research Director at NSS Labs.
“These results clearly demonstrate protection deficiencies for many vendors when their products are configured with default 'out-of-the-box' settings, which are what’s most commonly employed in the consumer market.”
“This test revealed that numerous vendors that protected against an exploit over HTTP failed to protect against the same exploit delivered via HTTPS,” said Bob Walder, Chief Research Officer at NSS Labs.
"Vendors who did not perform well might want to reconsider their default settings in this age of attacks against SSL and other protocols.”
“There are additional concerns for the enterprise,” Abrams adds.
“Enterprises embracing the ‘bring your own device’ (BYOD) approach to workplace technology need to be aware of the ramifications the product selection choices their users make, as they impact the organization’s security posture and attack profile.”
NSS Labs is currently running in-depth consumer end point protection (EPP) group testing that will further test all 13 vendors in several key areas – exploits, evasions, performance and protection against live malware, drive-by attacks and phishing.
Reports featuring the results for each test area will be released as testing is completed – reports for exploits, evasions and performance are targeted for release in September 2012.
Tested products:
Avast Internet Security 7
AVG Internet Security 2012
Avira Internet Security 2012
CA Total Defense Internet Security Suite
ESET Smart Security 5
F-Secure Internet Security 2012
Kaspersky Internet Security
McAfee Internet Security 2012
Microsoft Security Essentials
Norman Security Suite Pro
Norton Internet Security 2012
Panda Internet Security 2012
Trend Micro Titanium + Internet Security.
Overview
NSS Labs conducts significant research on the capabilities of endpoint protection (AV) products. As NSS
researchers were preparing for the impending Consumer Endpoint Protection Group Test, two critical
vulnerabilities against popular Microsoft products were disclosed. The first vulnerability resides within Microsoft
XML Core Services 3.0, 4.0, 5.0, and 6.0 and the second within Internet Explorer 8. Microsoft has since delivered
critical patches for both CVE’s in June and July 2012, respectively.
Unfortunately, exploits against both vulnerabilities are already being observed in the wild, and users that have
not yet patched their systems are at risk. Many users who have not yet patched, or have delayed patching,
assume their endpoint protection suite is defending their system in the interim.
The mission of endpoint protection is to defend users against exploits and malware when a patch is not available
or has not yet been applied. NSS Labs conducted testing on 13 popular consumer anti-virus (AV) products, to
see how well they repelled attacks on systems not yet patched for the CVE-2012-1875 and CVE-2012-1889
vulnerabilities.
Consumer-grade AV products that offer effective protection against these vulnerabilities allow users time to
patch systems (particularly important in enterprise environments with “bring your own device” (BYOD) policies in
place.) However, the successful exploitation of either of these critical vulnerabilities would reflect a significant
product failure, especially given the high profile and critical nature of these vulnerabilities.
NSS Labs Findings:
• Consumers who delay patching, or fail to patch more than their operating system alone, are at elevated risk
of compromise.
• Only 4 of the 13 products blocked all attacks; exploit prevention remains a challenge for most products.
• More than half of the products failed to protect against attacks over HTTPS that were blocked over HTTP, a
serious deficiency for a desktop AV / host intrusion prevention system (HIPS.)
• Where BYOD policies are in place in enterprise environments, delays in patching leave corporate networks at
serious risk of compromise.
• NSS Labs researchers are not the only ones testing security products - criminal organizations also have
sophisticated testing processes in order to determine which product detects which malware, and how the
various products can be evaded. Some crimeware will include various one-click buttons to “Bypass Vendor
X,” for example.
NSS Labs Recommends:
• Users of products that failed to block these attacks should update/patch immediately or otherwise mitigate.
• Where feasible, do not rely on AV software alone to protect your system; install a HIPS product or “Internet
security” suite (AV+HIPS) to provide an additional layer of protection.
• Enterprises with BYOD policies should carefully monitor for unpatched systems and consider enforcing
defense in depth strategies (“Internet security” suites, for example) on all BYOD systems.
• Users of Gmail, Facebook, and other services that utilize HTTPS should consider endpoint protection (AV)
products that can defend against threats being transported across this protocol.
• Consumers should consider using patch management tools such as the Secunia Personal Software
Inspector
Analysis
NSS Labs conducted testing on 13 popular consumer anti-virus (AV) products, to see how well they repelled
attacks on systems not yet patched for the CVE-2012-1875 and CVE-2012-1889 vulnerabilities. The successful
exploitation of either of these critical vulnerabilities can result in arbitrary remote code execution by the attacker,
thus posing a significant threat to users.
To test the antivirus products, NSS Labs researchers crafted one payload containing shellcode to launch
calc.exe, and a second payload that invoked a reverse Meterpreter shell over HTTPS. Additional testing was
done to see if the products could easily be disabled upon successful exploitation of the vulnerability and if basic
obfuscation tactics would defeat protection.
Raw exploits were augmented with common evasion tactics, such as Base 64, Unicode, and Javascript
encoding. In addition to attacks over HTTP, NSS Labs also used the HTTPS protocol.
Three distinct patterns of capabilities begin to emerge throughout this test. However a much more
comprehensive end-point protection test, scheduled for completion later this year, will provide a better indication
of comparative capabilities of the products.
One surprising finding was that Base 64, Unicode, and Javascript encoding failed to trip up antivirus products
as they have in previous NSS Labs tests. NSS Labs researchers will include several more evasions in the endpoint
product tests later this year.
Basic Exploit Protection
The first test was to see which products could block the exploitation of two recent, high-risk vulnerabilities and
identify at which stage the product stopped the attack. Did the product block the exploit from triggering the
vulnerability or simply the content delivered by the exploit? Avast, AVG, Avira, ESET, Kaspersky, McAfee,
Norton, and Trend Micro all blocked both attacks against CVE-2012-1889 when NSS engineers attempted to
exploit the two vulnerabilities.
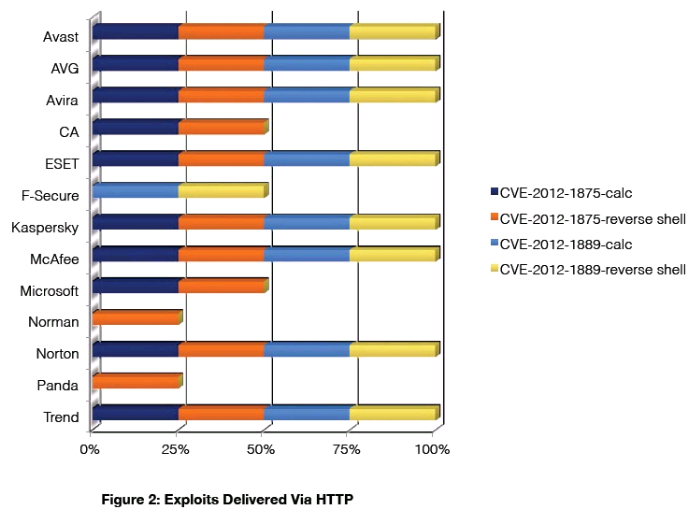
F-Secure blocked both exploits against CVE-2012-1889 while failing to prevent either exploit against CVE-2012-
1875. Conversely, CA and Microsoft blocked both attacks against CVE-2012-1875, while failing to prevent
either exploit against CVE-2012-1889. Norman and Panda also failed to prevent both exploits against CVE-2012-
1889 and blocked only one of the two exploits against CVE-2012-1875, indicating that their protection relies on
detecting the malicious content being delivered after an exploit has successfully compromised the system as
opposed to preventing the exploit itself.
The World Is Going To HTTPS / SSL
In addition to banking and e-commerce sites, HTTPS is being used exclusively by some of the most popular
Internet-based applications such as Google’s webmail service, Gmail.
For the next phase NSS Labs researchers transmitted the exploits over an encrypted channel using the HTTPS
protocol. In these tests, only Avast, Kaspersky, McAfee, and Trend Micro successfully blocked both exploits
while nine (9) of the 13 products fully or partially failed to protect the victim.
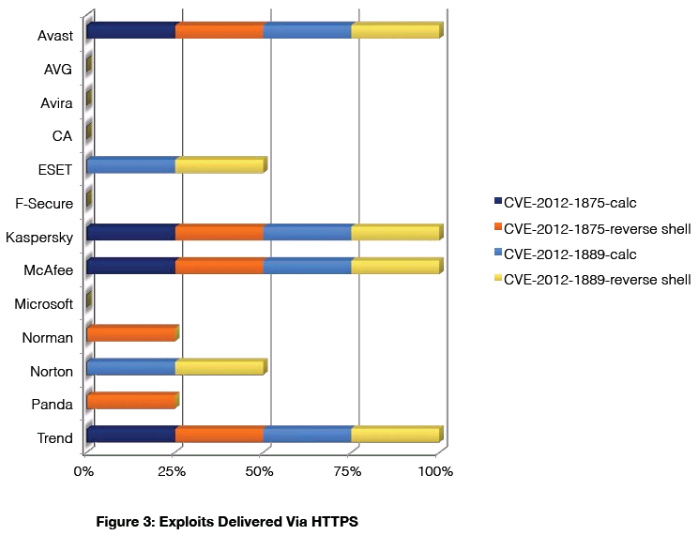
AVG, Avira, CA, F-secure, and Microsoft failed to block any of the exploits, even though they had partial, or even
complete, success in blocking the same attack when delivered over HTTP, indicating a failure to implement
protection against exploits delivered via HTTPS. ESET and Norton failed to block both attacks against CVE-
2012-1875 when delivered via HTTPS, indicating a flaw in how the products handle attacks delivered via HTTPS
against the browser itself.
Where attackers elect to use SSL, it is quite possible that even known malware will slip past the faulty intrusion
prevention found in these products.
En Garde
Once an endpoint defense mechanism of any kind has been bypassed, the next step taken by most attackers is
to attempt to disable it completely. This would, for example, enable further malicious software to be downloaded
without risk of it being detected by the protection mechanism.
There are significant differences in the abilities of market-leading products to defend themselves against being
disabled. Unfortunately both Microsoft and CA offerings presented virtually no defensive capabilities. Both
products could be disabled with a simple “kill” command.
Other products presented varying degrees of resilience and full details will be in the reports of the EPP testing
results in late 2012.
The Good, The Bad, And The Ugly
Avast, Kaspersky, McAfee, and Trend were able to block all four attempted exploits when delivered via HTTP or
HTTPS protocols. ESET and Norton both blocked the four initial attacks, but when HTTPS was added to the mix
they failed to block either attack exploiting CVE-2012-1875. AVG and Avira both blocked all four attempted
exploits, but were unable to deal with the HTTPS variations.
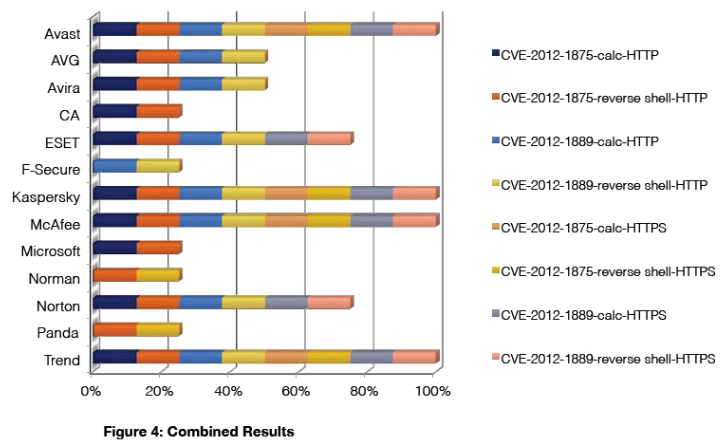
CA, Microsoft, Norman, and Panda, were all able to block only two of the eight total variations of the attacks.
While Norman and Panda only blocked one exploit over HTTP, the same exploit was blocked over HTTPS,
indicating that HTTPS does not appear to be an issue for either product.
The combinations of failures and successes are dramatic and necessitate further research. It is clear that many
of the products are not blocking exploits. However, more testing is required to determine if those that scored
well in this test had signatures for calc.exe and Meterpreter traffic, or actually block the exploits regardless of
payload.
The failure to deal with HTTPS would seem conclusive, but NSS Labs will further validate the results in more
comprehensive testing that will include a several more exploits and a battery of new and existing malware, both
known and unknown to the products under test.
Zaloguj
lub
Zarejestruj się
aby zobaczyć!


 jeśli będzie chodził lekko jak NIS...do tego czasu powinni w ogóle wstrzymać dystrybucję tej kobyły,która potrafi przymulić najlepsze maszynki
jeśli będzie chodził lekko jak NIS...do tego czasu powinni w ogóle wstrzymać dystrybucję tej kobyły,która potrafi przymulić najlepsze maszynki 